AWS Certified Security - Specialty - Exam Simulator
SCS-C02
Advance your career in cloud cybersecurity with the AWS Certified Security - Specialty Exam Simulator! Tailored for professionals, this tool offers realistic practice exams to mirror the official exam.
Questions update: Jun 06 2024
Questions count: 5439
Example questions
Domains: 6
Tasks: 22
Services: 26
Don't be fooled by the relatively short list of exam scope services. You really have to know them all in great detail. Each service is integrated with others and encompasses countless concepts and technologies you must be well familiar with.
The AWS Certified Security - Specialty certification is known for its high level of difficulty, requiring both broad and deep knowledge of security principles and AWS services. This certification tests your ability to secure applications and data on the AWS platform, demanding a thorough understanding of core security services and best practices for securing AWS environments.
The exam emphasizes an understanding of key AWS security services such as IAM, KMS, CloudTrail, Config, Shield, WAF, Security Hub, and GuardDuty. You need to know how these services work, how to configure them, and how to integrate them into a secure architecture.
You must be able to solve complex, real-world security problems. This includes designing secure infrastructures, implementing robust access controls, managing data protection, and performing incident response. Understanding how to monitor and audit AWS environments for compliance and security issues is also essential, involving tools like CloudWatch, CloudTrail, and AWS Config.
Regulatory compliance is another critical aspect. Candidates must understand various regulatory requirements such as HIPAA, GDPR, and PCI-DSS, and how to implement and maintain compliance within AWS environments. This includes using AWS services to meet these regulatory standards and setting up audit trails and monitoring systems to ensure ongoing compliance.
The certification also requires a solid grasp of AWS's global infrastructure, including regions and availability zones, and how to design applications that ensure high availability, fault tolerance, and disaster recovery.
Furthermore, the exam demands familiarity with advanced security practices, including encryption mechanisms, secure data storage and transfer, and identity and access management. You need to understand how to leverage these practices to protect sensitive data and maintain security across various AWS services.
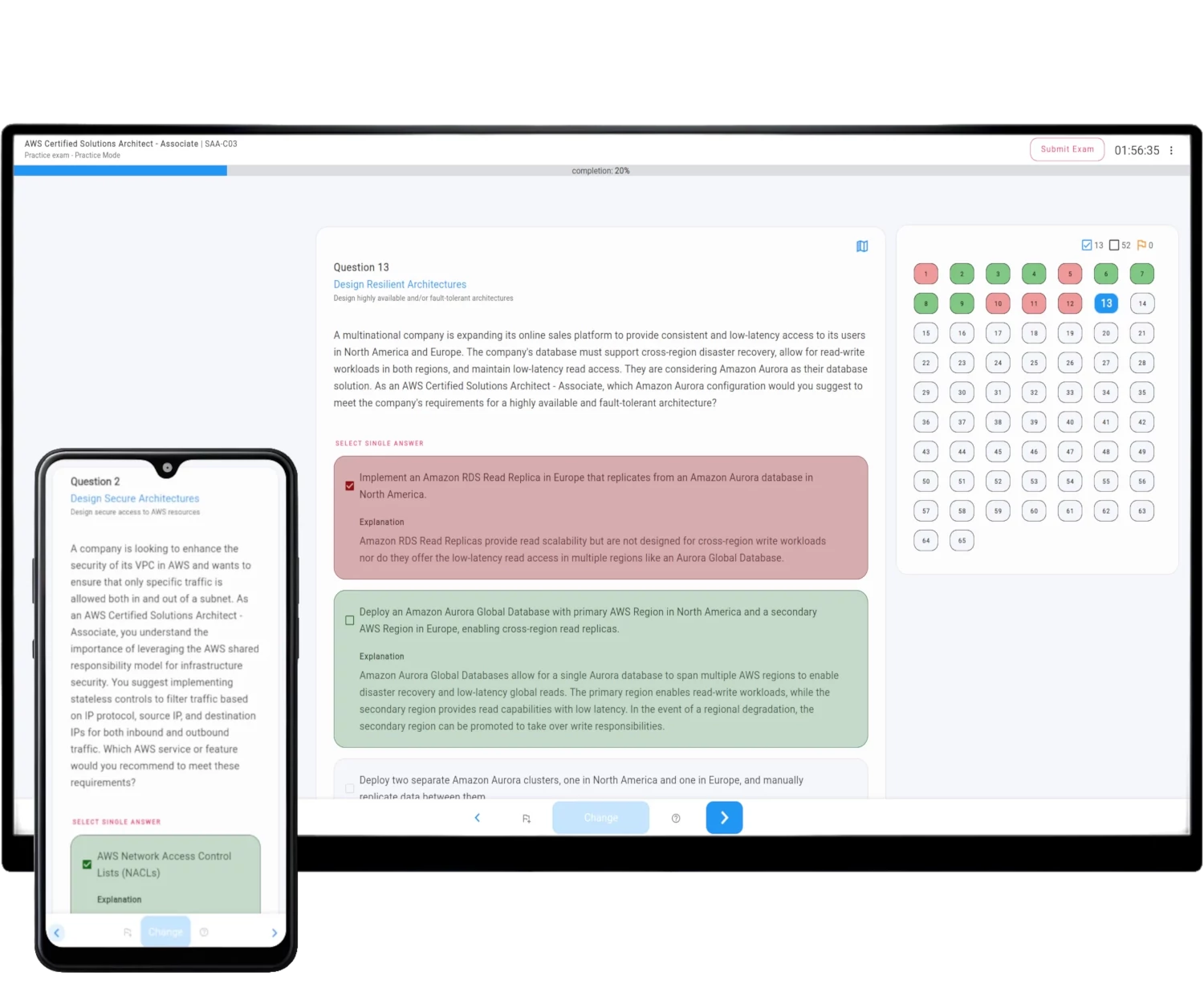
How AWS Exam Simulator works
The Simulator generates on-demand unique practice exam question sets fully compatible with the selected AWS Official Certificate Exam.
The exam structure, difficulty requirements, domains, and tasks are all included.
Rich features not only provide you with the same environment as your real online exam but also help you learn and pass AWS Certified Security - Specialty - SCS-C02 with ease, without lengthy courses and video lectures.
See all features - refer to the detailed description of AWS Exam Simulator description.
| Exam Mode | Practice Mode | |
|---|---|---|
| Questions count | 65 | 1 - 65 |
| Limited exam time | Yes | An option |
| Time limit | 170 minutes | 10 - 200 minutes |
| Exam scope | 6 domains with appropriate questions ratio | Specify domains with appropriate questions ratio |
| Correct answers | After exam submission | After exam submission or after question answer |
| Questions types | Mix of single and multiple correct answers | Single, Multiple or Both |
| Question tip | Never | An option |
| Reveal question domain | After exam submission | After exam submission or during the exam |
| Scoring | 15 from 65 questions do not count towards the result | Official AWS Method or mathematical mean |
Exam Scope
The Practice Exam Simulator questions sets are fully compatible with the official exam scope and covers all concepts, services, domains and tasks specified in the official exam guide.
For the AWS Certified Security - Specialty - SCS-C02 exam, the questions are categorized into one of 6 domains: Threat Detection and Incident Response, Security Logging and Monitoring, Infrastructure Security, Identity and Access Management, Data Protection, Management and Security Governance, which are further divided into 22 tasks.
AWS structures the questions in this way to help learners better understand exam requirements and focus more effectively on domains and tasks they find challenging.
This approach aids in learning and validating preparedness before the actual exam. With the Simulator, you can customize the exam scope by concentrating on specific domains.
Exam Domains and Tasks - example questions
Explore the domains and tasks of AWS Certified Security - Specialty - SCS-C02 exam, along with example questions set.